Closing the Harvesting Gap

Abstract: Combining multi-THz optical spectrum spreading, photonic phase encoding, and negative optical signal-to-noise ratio (OSNR) transmission forms a photonic shield that prevents data recording and harvesting for offline deciphering. This supports post- quantum security by eliminating raw data availability for quantum computers processing
The PLS method is based on the following photonic tripod manipulation: (1) multi-THz optical spectrum spreading by the use of a mode-locked laser (MLL), (2) optical phase encoding by applying an encryption code forming the optical key, and (3) generating negative OSNR conditions by burying the optical signal below a strong amplified spontaneous emission (ASE) noise source. In turn, this photonic-tripod manipulation results in a “noise-like” signal transmission spanned over a multi-THz analog bandwidth.
Detection and recording of the signal require prior knowledge of the optical key; otherwise, the signal will be destroyed and lost during the optical-to-electrical conversion process. Consequently, the proposed cybersecurity PLS is the first and only technology that prevents the possibility of harvesting data in transit through optical fibers.
The following comparison table provides a concise, side-by-side technical perspective on Photonic Layer Security (PLS), Quantum Key Distribution (QKD), and Post-Quantum Cryptography (PQC). The comparison is structured to reflect fundamentaldifferences in security anchoring (physical layer versus cryptographic layer), protection scope, infrastructure requirements, and operational implications. Rather than evaluating individual algorithms, the table contrasts the security models and deployment realities of each approach, with particular emphasis on data-in-transit exposure, post-quantum readiness, and practical network integration. This enables an objective assessment of how each technology addresses long-term confidentiality risks in optical communication systems.
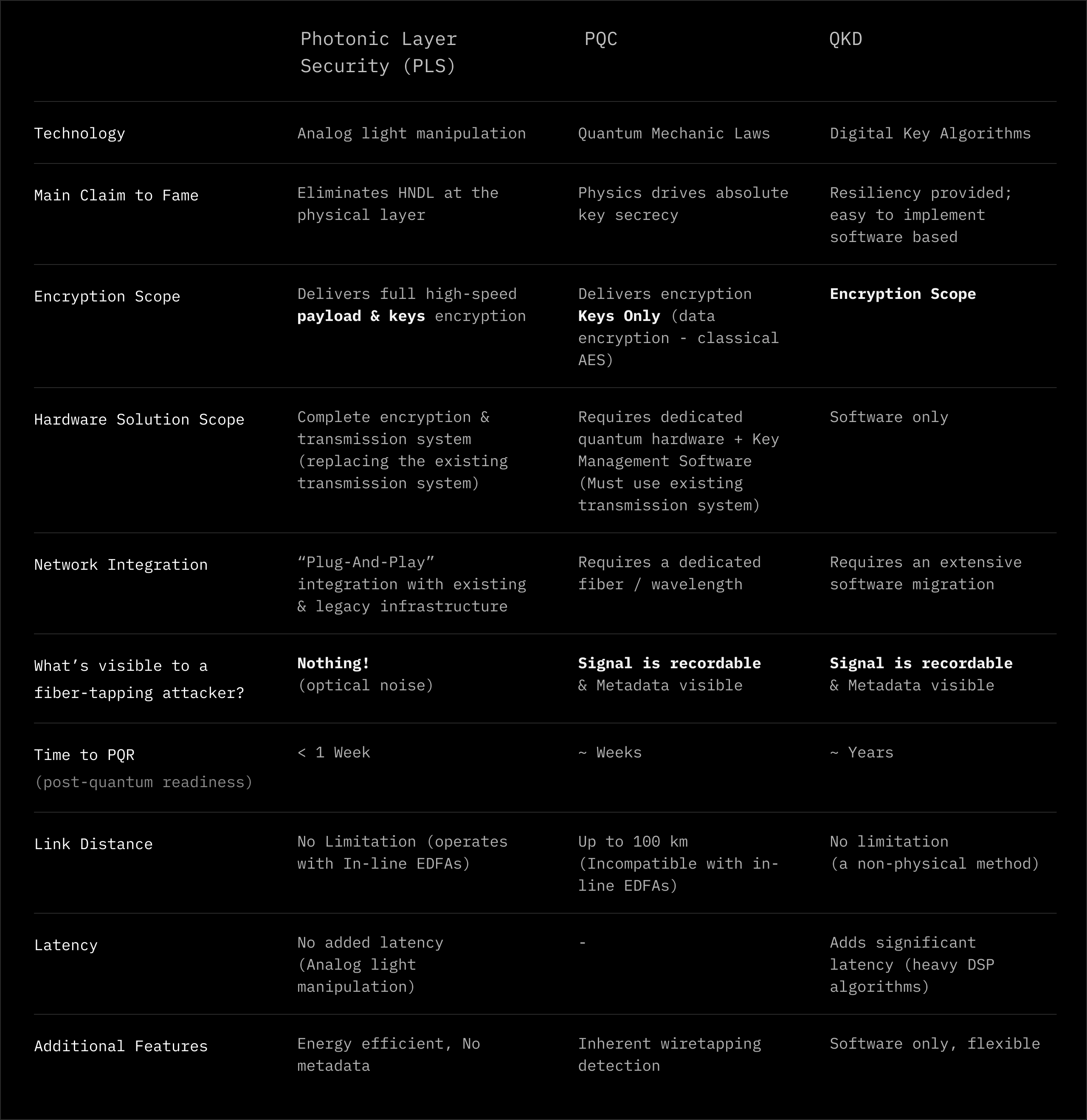
Table Summary
The comparison highlights a fundamental distinction between non- recordable and recordable security models. PLS uniquely secures the optical signal itself, preventing data capture and offline harvesting during transmission and thereby eliminating the feasibility of harvest-now-decrypt-later attacks, thereby closing the Harvesting Gap by definition.
By contrast, both QKD and PQC can be characterized as recordable encryption solutions: while QKD protects key establishment using quantum mechanics and PQC strengthens cryptographic algorithms against future quantum attacks, in both cases the transmitted data stream remains recordable and available for long-term storage and potential future analysis. As a result, PLS provides immediate post- quantum protection at the physical layer, whereas QKD and PQC rely on cryptographic assumptions and operational controls to mitigate risks associated with recorded data.

